Vanilla Tempest INC Ransomware Menace in Healthcare.
“Microsoft Exposes ‘Vanilla Tempest’: A New Ransomware Threat Targeting U.S. Healthcare Sector” **Exploring the Rise of INC Ransomware
Read more“Microsoft Exposes ‘Vanilla Tempest’: A New Ransomware Threat Targeting U.S. Healthcare Sector” **Exploring the Rise of INC Ransomware
Read more“Unmasking Hidden Dangers: Weaponized PDFs and SambaSpy’s Stealthy Assault on Windows Users” **Weaponized PDFs and SambaSpy: A Deep
Read more“Exploiting Trust: How Threat Actors Turn Legitimate Software into Cyber Weapons” **Exploring the Rise of CAMO Attacks: How
Read more“Global Vigilance: Thwarting GRU Cyber Threats to Protect Integrity and Security” Analyzing the Impact and Strategy of GRU
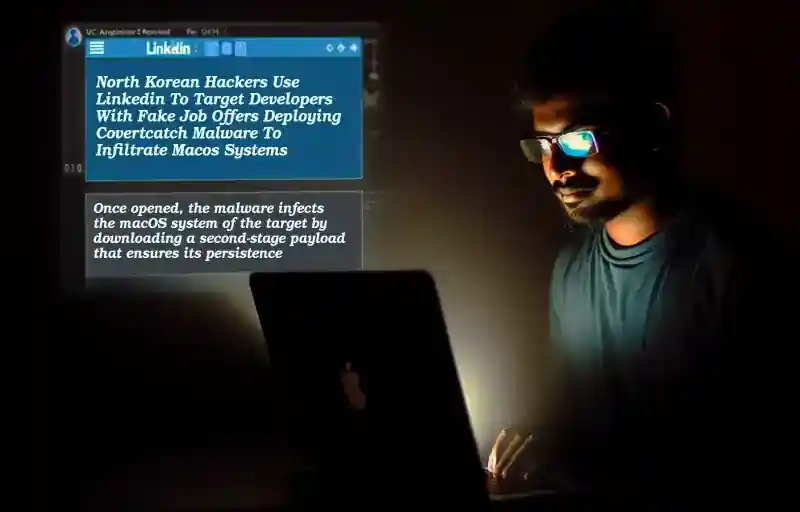
Read more“North Korean Hackers Use LinkedIn to Launch Fake Job Scams, Targeting Developers with Malware-Infected Coding Tests” North Korean
Read more“Discord and Telegram: Not Just for Chatting, a Playground for Cybercriminals” **Exploring the Dark Side of Discord and
Read more“Red Teaming Tool Misused: Threat Actors Deploy MacroPack for Malware Delivery, Reveals Cisco Talos” Exploring the Misuse of
Read more“Emansrepo: Stealthy Python Infostealer Evolving Rapidly to Compromise Data through Ingenious Phishing Tactics” Understanding Emansrepo: A New Python
Read more“Outsmarting Sophistication: Unmasking ViperSoftX’s Use of Common Tools in Advanced Cyber Threats” How Sophisticated Threat Actors Utilize Common
Read more“Unmasking Head Mare: Exposing Systemic Vulnerabilities and Evading Detection with Precision” Exploring the CVE-2023-38831 Vulnerability: How Head Mare
Read more