North Korean Hackers Target Finance with Chrome Vulnerability
“North Korean Cyber Threat: Exploiting Zero-Day Flaws in Google Chrome and Windows to Deploy FudModule Rootkit” North Korean
Read more“North Korean Cyber Threat: Exploiting Zero-Day Flaws in Google Chrome and Windows to Deploy FudModule Rootkit” North Korean
Read more“Unveiling the Shadows: Cyber Espionage Campaign Exploits Google Sheets in Global Malware Blitz” Exploring the Use of Google
Read more“Stay Alert, Stay Safe: Don’t Let ‘Bull Checker’ Drain Your Crypto Wallets!” The Rise of Malicious Browser Extensions:
Read more“Turning Tools into Traps: How Cybercriminals Exploit Digital Marketing Technologies for Malicious Gain” The Rise of Cybercriminals Using
Read more“RansomHub: Mastering Double Extortion in the Digital Shadows” **Exploring the Rise of RansomHub: A Deep Dive into Its
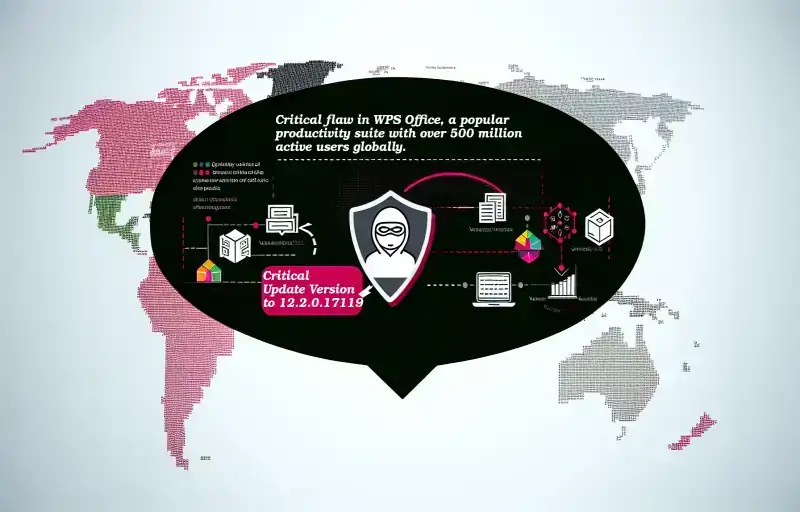
Read more“Secure Your Work: Update WPS Office to Guard Against Advanced Cyber Threats” **Exploring the Impact of Command Line
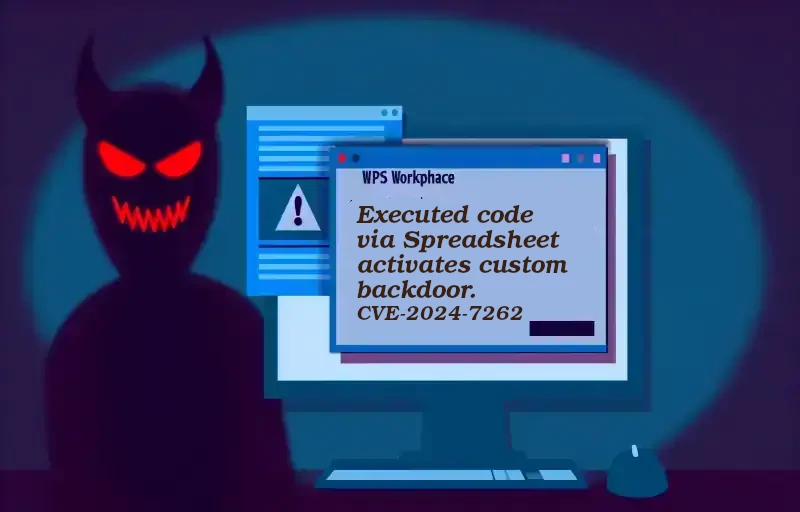
Read more“Unveiling CVE-2024-7262: A Critical WPS Office Flaw Exploited by APT-C-60 to Deploy SpyGlace Malware” Analyzing CVE-2024-7262: A Deep
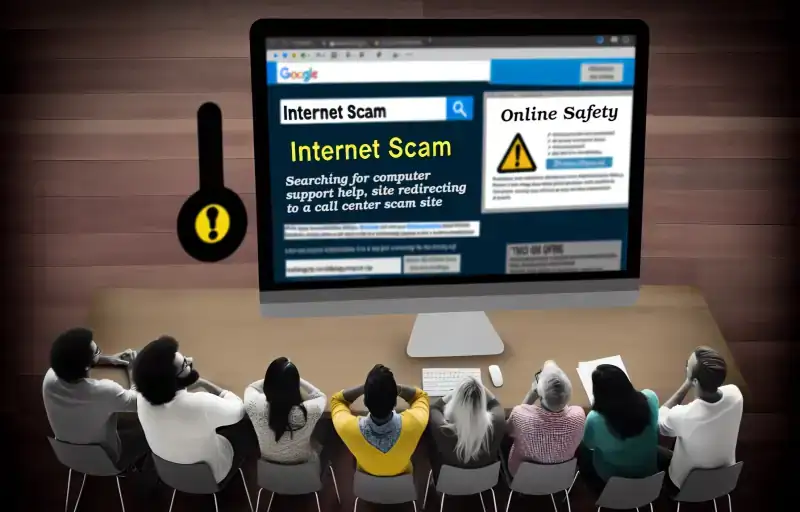
Read more“Stay Safe Online: Beware of Microsoft Search Query Scams—Don’t Let Fraudsters Trick You into Costly Calls!” Understanding Microsoft
Read more“Guard Against Deception: Beware of Fake Helpdesk Scams on Microsoft Learn” Exploring the Dangers of Fake Helpdesk Scams
Read more“Evading Detection, Ensuring Persistence: Exploring Advanced Malware Techniques in ‘Crypted.bat’” Advanced Replacement Techniques in Malware: Exploring Crypted.bat and
Read more