How CAMO Attacks Exploit Legitimate Software for Cybercrime.
“Exploiting Trust: How Threat Actors Turn Legitimate Software into Cyber Weapons” **Exploring the Rise of CAMO Attacks: How
Read more“Exploiting Trust: How Threat Actors Turn Legitimate Software into Cyber Weapons” **Exploring the Rise of CAMO Attacks: How
Read more“TrickMo: Stealthy Android Banking Malware Unleashed, Guard Your Credentials and Secure Your Device!” Understanding Android Banking Malware: A
Read more“Unshielded Targets: How CosmicBeetle Exploits Weak SMB Defenses with ScRansom” **Understanding CosmicBeetle: A Deep Dive into Its Exploitation
Read more“Unit 42 Exposes New Phishing Frontier: Stealth Attacks via HTTP Header Refresh” Emerging Threats: How Cybersecurity Researchers at
Read more“Microsoft’s September 2024 Patch Tuesday: Securing Systems with Fixes for 79 Vulnerabilities, Including Four Critical Zero-Days.” Analyzing Microsoft’s
Read more“Chinese-linked Tidrone Espionage: Targeting Taiwan’s Military and Satellite Sectors with Sophisticated Cyber Attacks” Exploring the Tactics of Tidrone:
Read more“Global Vigilance: Thwarting GRU Cyber Threats to Protect Integrity and Security” Analyzing the Impact and Strategy of GRU
Read more“Empowering Cybersecurity: U.S. Government Embraces Skills Over Degrees to Secure the Nation” Impact of the Serve for America
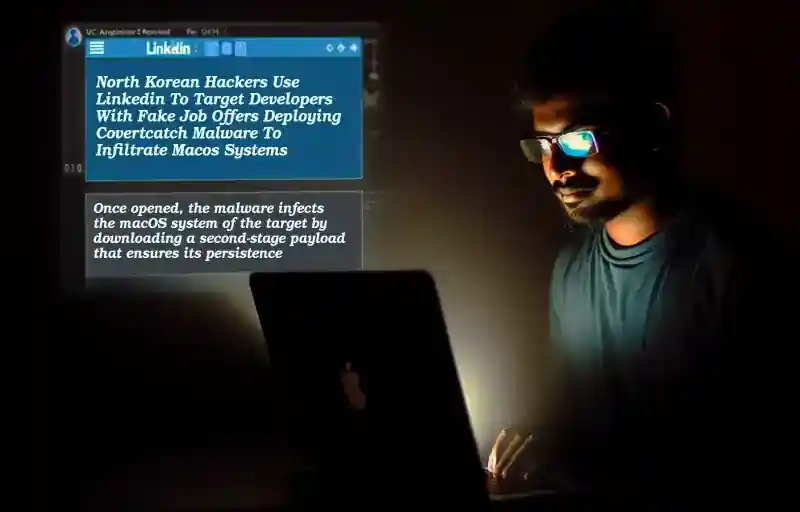
Read more“North Korean Hackers Use LinkedIn to Launch Fake Job Scams, Targeting Developers with Malware-Infected Coding Tests” North Korean
Read more“Discord and Telegram: Not Just for Chatting, a Playground for Cybercriminals” **Exploring the Dark Side of Discord and
Read more